ASSESSMENT SCENARIO
A conveyancing & estate service in the UK, CONVXYZ, hired your team to set up their IT network/system. The company provides (i) real estate services for property vendors and buyers and (ii) conveyancing services by their employed lawyers. The goal of the security system is to prevent or minimize the business loss caused by possible incidents, such as malfunction, information stealing, data modification, deletion or destruction, etc., including the recent dangerous conveyancing scams that has several victims recently.
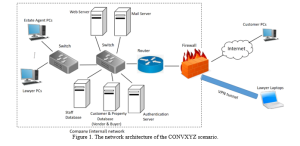
Your colleagues in the team have proposed the first version of the security network architecture depicted in Figure 1. As a person responsible for risk assessment in your team, your task is to conduct a risk assessment on this system.
In Figure 1 the internal network of CONVXYZ is denoted by the dashed box, and all the assets in this dashed box are located in the company premise in the UK.
In Figure 1 the internal network of CONVXYZ is denoted by the dashed box.
- The company has a website (by the web server) where the customers can browse the properties and contact the estate agents. After registering to their conveyancing service, the customers get an account (username and password) to the website with which they can login and keep track of their property selling/buying transaction e.g., download documents for signing, upload their documents.
- The authentication server is responsible for authenticating the credentials (usernames and passwords) of both the customers and staff (lawyers and estate agents). When performing an authentication task, the authentication server communicates with the customer and staff database which stores information about the customers and staff. After a successful authentication, the customers and staff will be able to access to their property selling/buying documentations and current transaction/status.
- Company employees, such as lawyers and estate agents can use their computers to login the company website or browsing the internet.
- Before property exchange between the vendor and buyer, the buyer is requested to transfer the money to the bank account of CONVXYZ. The bank account details is sent to the customer via email or by post.
- The mail server enables staff to send and receive emails from the customers and other member of staff.
- Individual visitors/customers can browse the website of CONVXYZ and register/login with their PCs via Internet.
- Lawyers are allowed to work remotely via a VPN (Virtual Private Network) tunnel.
- The PCs and servers are connected to 2 network switches and a router.
- The internal network is protected by a firewall.
Figure 1. The network architecture of the CONVXYZ scenario.
[1] https://www.theguardian.com/money/2017/jan/14/lost-67000-conveyancing-scam-friday-afternoon-fraud-legal-sector-email-hacker
ASSESSMENT BRIEF
In this assignment you have to:
- Conduct a risk assessment on the network in Figure 1, based on the ISO 27005 standard.
- Write a detailed risk assessment report (see Section 4 for the required structure).
FLEXIBILITY OF THE SOFTWARE/HARDWARE/FIRMWARE PARAMETERS
As you can see, there are no specific hardware and software details given in Figure 1. To avoid working in the entirely same network (and hence copying from each other), before doing the risk assessment, you have to specify the system parameters and the system boundaries, including the used operating systems, hardware, software/applications and firmware. Ideally, each of you will work with different sets of system parameters/scope that you chose or specified.
Expert's Answer
Chat with our Experts
Want to contact us directly? No Problem. We are always here for you

Get Online
Assignment Help Services