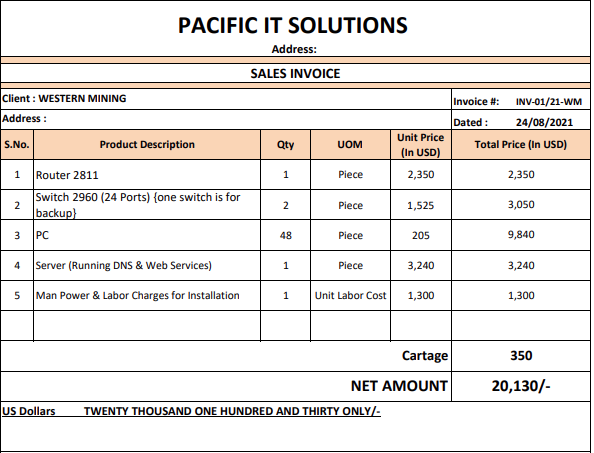
Task 1
Q1.Write a detailed description of the client's requirements
A meeting was held at Western Mining Head Office with one of our long-time customers Western Mining representatives for their Branch Office Network Initiation in Brisbane, in which below mentioned people from their side were present:
JTK -> James T. Kirk, Manager, Western Mining
DT -> Deana Troy, Senior Systems Architect, Western Mining
JC -> Jack Crusher, Branch Office Manager, Western Mining &
I -> IT Consultant, Pacific IT Solution Pty. Ltd.
In that meeting, they gave me a clear picture and roadmap for the installation of network infrastructure at their Brisbane branch office. Everybody told me their requirements which they wanted in the network infrastructure. The detailed explanation of requirements which they told me is mentioned below:
1. The branch office will initially have a small number of staff but it could increase in future. So it means that whatever the network my team alongwith me will be designing and deploying for branch office must have the scalability option available. So if the number of end-users (staff) increases in future, then they will not be facing any issue at that moment.
2. The network design must allow upto 510 staff members / department. This means that I have to design a network in which the number of assignable IPs or assignable host IPs must cater the need of 510 staff members per department.
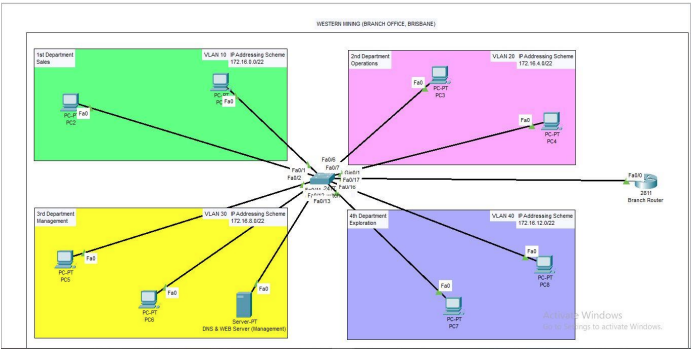
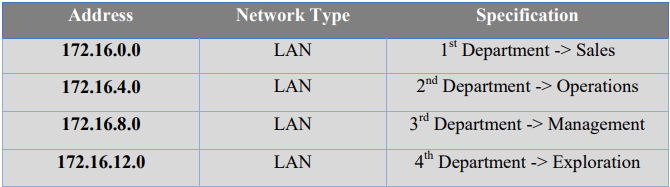
3. There will be 4 departments at branch office, Brisbane ie Sales, Operations, Management, & Exploration. So, whatever the network design we will be designing for them, we have to take care that it must cater the need of 4 departments.
4. In security requirements, they wanted that management department’s server must not be left accessible from all other departments for security reasons but management department’s staff and server administration can access to every single PC, Server, & Switch present on a branch network. This means we have to configure an extended ACL and have to block all the traffic coming for the destination of management’s server and have to bind it on the interface of the router to which management department’s LAN is connected.
5. Then, they directed us to follow the IP addressing scheme of 172.16.0.0/16 as they were having 172.20.0.0/16 network at their head office. So, in order to assign 172.16.0.0/16 network to 4 departments, we have to perform subnetting by dividing this 172.16.0.0/16 network into 4 subnetworks or baby networks.
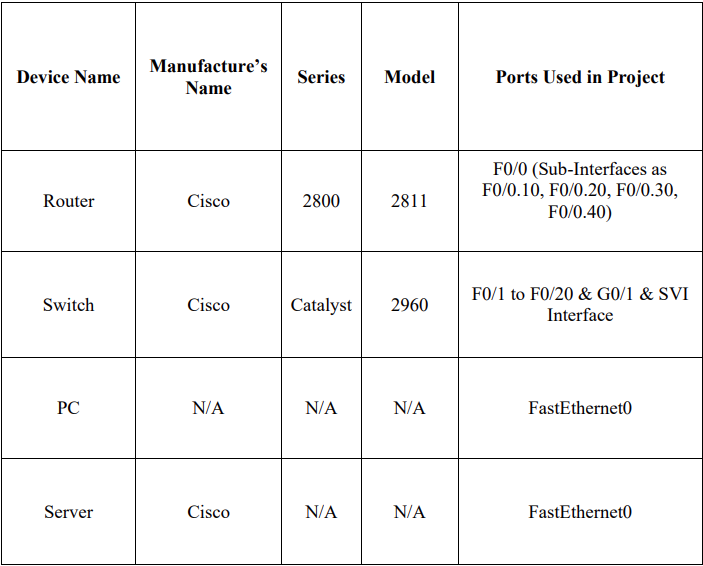
6. Then, we were directed to use only a single Cisco Router of 2800 series which is Router 2811 and multiple switches Cisco Catalyst 2960.
7. Then they asked us to provide remote access of branch office intermediary devices from head office.
To fulfill this requirement, we have to configure SSH on every single intermediary device like Routers & Switches.
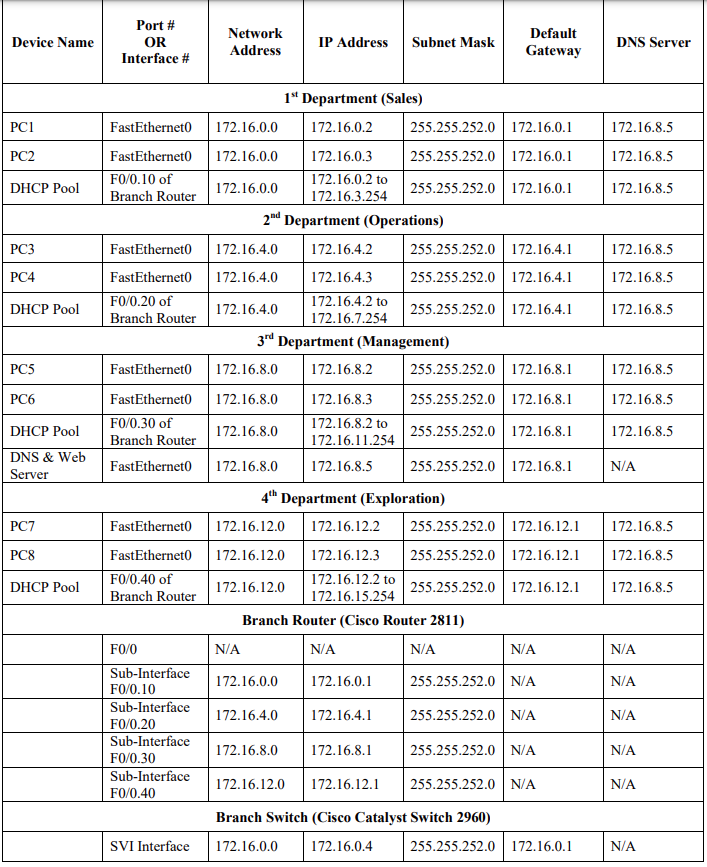
8. Then, we were directed to assign IP address to the end devices dynamically throughout the branch office network. For that, we have to configure DHCP Server in every department and have to create a pool of relevant IP addresses for each department.
9. Then it was directed that WAN links must also be configured by us. So, we have to configure a local network at one end of the WAN Router and also make the connectivity between the local departments network and WAN / Internet / Cloud / ISP.
10. They said they want to run OSPF throughout the network. For that, we have to perform dynamic routing between LAN and WAN and the protocol which will be used is Open Shortest Path First (OSPF).
Task 2:
Write a detailed description of the network you will provide including security and WAN functionality.
The network which Pacific IT Solutions will provide to its long-time customer Western Mining will have the following mentioned description:
Wired technology will be used across the network. No wireless technology will be used in the branch office network as per the requirements of the company’s stakeholders.
The cabling that will be used throughout the branch office network will be Shielded Twisted Pair (STP) copper cabling CAT7 which gives 10Gbps speed across the network.
The switches that will be used in network are Cisco Catalyst 2960 and initially they will be in total of 1, and that will be the main switch of the branch named as Branch Switch because at start, there will be less number of users but as the number of users / staff members / employees will increase, we can connect more switches because the network which we have designed for our client is scalable. So, we can connect more switches in future due to the scalability of our network.
The main switch is having 4 VLANs configured in it and the names of the VLANs are: 1) Sales VLAN, Operations VLAN, Management VLAN, & Exploration VLAN. Each and separate VLAN has been created for separate department.
Inter-VLAN routing will be performed using the concept of “Router-on-a-Stick”. In this concept, we basically create the sub-interfaces on router’s interface and then assign IP address to those subinterfaces along with the encapsulation command.
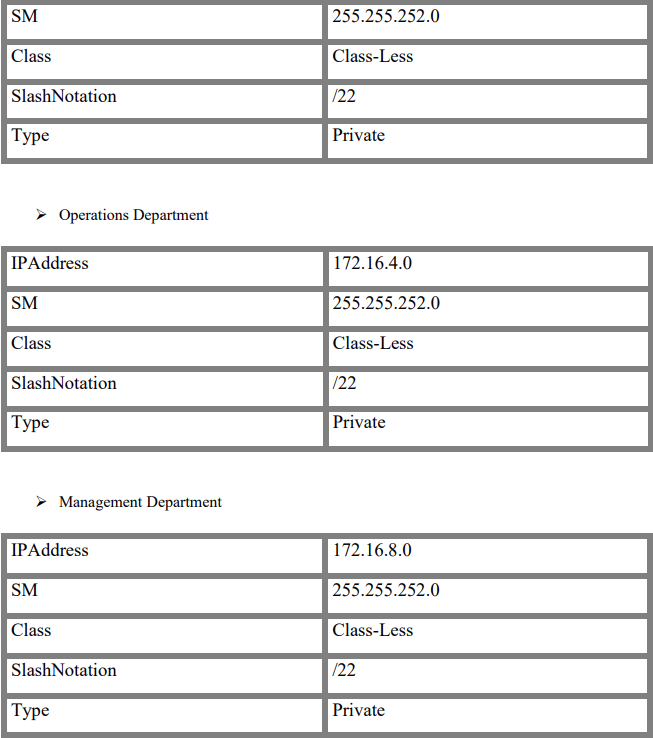
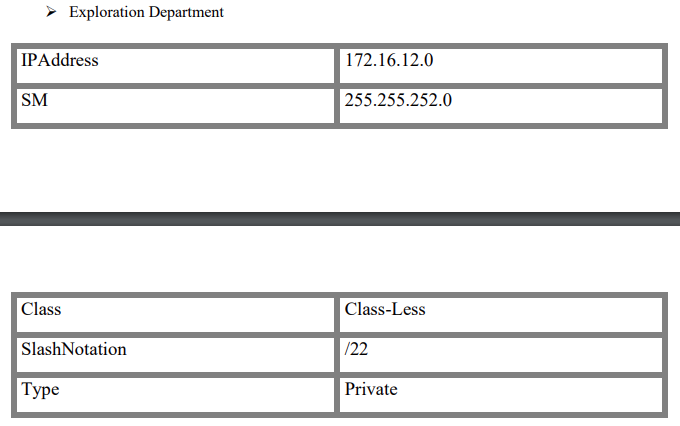
All the departments will be configured with private IP addressing and will have respective IP addressing schemes: Sales (172.16.0.0/22), Operations (172.16.4.0/22), Management (172.16.8.0/22), & Exploration (172.16.12.0/22).
Block Size of 4 ie 256-252 = 4 has been taken so that we can cover the need of 510 user per department and one IP address which will serve as the default gateway of every single LAN and two IPs for broadcast and network address. So, in total we will need 513 IP addresses to cater the requirement and for that purpose, we create the block size of 4 as 2 blocks can only cater 512 IPs.
Each department will have its DHCP pool created on relevant router’s sub-interface which will assign the IPs to the end devices dynamically.
The branch office will have the DNS and Web server configured at the management department on which the website of Western Mining will be hosted.
The branch office will have only one router in their entire local network and which will be of Cisco 2800 series, specifically as Cisco 2811 Router. To Cisco 2811, all the departments will be connected.
In order to secure the network, Extended Access Control List (ACL) will be configured on the network in order to filter out the external and hazardous/ malicious traffic.
All networking devices present on the network will be configured with the IP address in order to allow the remote access for the end-users through any protocol like Telnet (uses port 23) or SSH (Secure Shell, uses port 22).
Get Assignment Help from Me